With the rise of SaaS (Software as a Service) applications in businesses, the number of entry keys is multiplying, posing a real security problem. This article aims to raise awareness of the security risks associated with SaaS applications and to present an innovative technology as a solution.
The security risks of SaaS applications
SaaS applications present a number of vulnerabilities, including unauthorised access due to weak passwords, phishing techniques or security flaws. Cybercriminals exploit these weaknesses to access sensitive data, steal information or disrupt business operations.
Shadow IT, where employees use SaaS applications not approved by the company, is another major risk. These applications are beyond the control of the IT department, which can lead to leaks of sensitive data. Employees, looking to improve their productivity, may download and use applications without realising the associated security risks.
Data leaks can also occur as a result of inadequate security configurations, human error or targeted attacks. For example, misconfiguration of sharing parameters in a SaaS application can expose sensitive data to unauthorised third parties. These incidents compromise data confidentiality and can cause significant financial damage. In addition, businesses must comply with strict regulations such as GDPR, SOC, NIS2 and ISO. Failure to comply can result in fines, penalties and loss of reputation.
Internal threats posed by negligent employees represent a significant risk. These employees may abuse their access, share sensitive information or make mistakes that compromise security. For example, an employee may accidentally send a file containing sensitive information to the wrong person, or use an unsecured device to access SaaS applications.
In addition to these risks, SaaS applications can be vulnerable to Denial of Service (DDoS) attacks, where attackers overload the application’s servers with massive traffic, making the service unavailable to legitimate users. Vulnerabilities in the APIs (application programming interfaces) used by SaaS applications also represent a risk. Poorly secured APIs can be exploited by attackers to gain access to the application’s data and functionalities.
Finally, the risks associated with dependency on SaaS service providers should not be overlooked. If a SaaS provider suffers a security breach or outage, this can have a direct impact on business operations. Businesses need to carefully evaluate SaaS service providers and ensure that they meet high security standards.
Introducing SaaS Security Technology
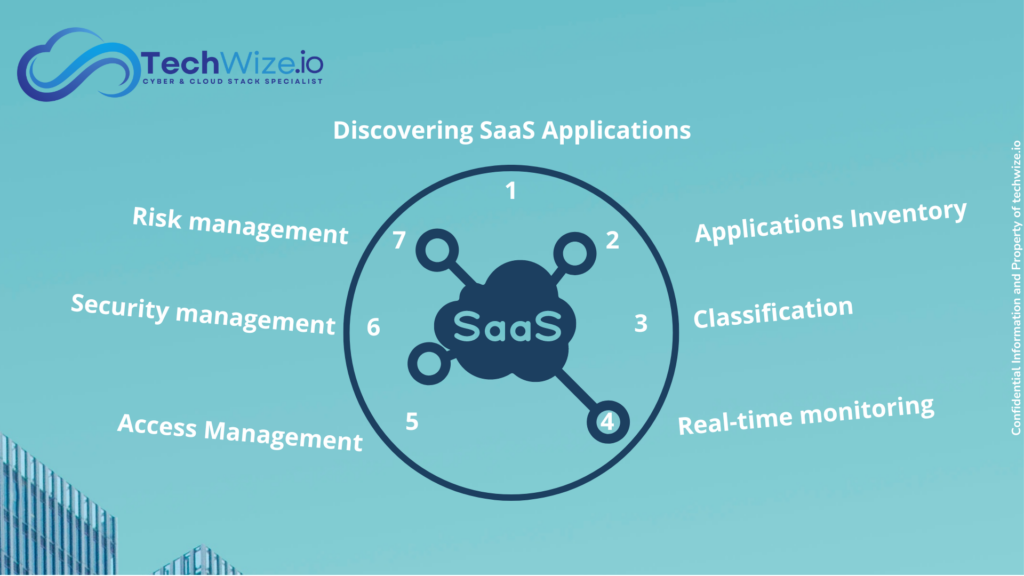
To manage and mitigate these risks, it is important to implement SaaS security technology. This solution enables businesses to protect sensitive data, ensure compliance and prevent cyber attacks. Security administrators and IT teams use this technology to discover SaaS applications, monitor their use in real time and manage access effectively.
SaaS application discovery
It scans the corporate environment to identify all SaaS applications in use, including unauthorised ones. It uses network traffic analysis and monitoring agents on user terminals to detect SaaS applications, even those that are not officially approved. This discovery creates a complete inventory of applications and associated users, making it easier to manage and secure applications.
Application inventory and classification
Once applications have been discovered, this technology creates a detailed inventory of SaaS applications and associated users. Applications are then classified according to their level of risk and compliance with corporate security policies. This classification enables security administrators to prioritise security measures and manage risks effectively.
Real-time monitoring
SaaS continuously monitors the use of SaaS applications and detects anomalies and suspicious behaviour. It sends real-time alerts to security managers as soon as suspicious activity is detected. This continuous monitoring enables potential threats to be identified quickly and a rapid response to prevent security incidents.
Access management and authentication
Access management is a crucial aspect of SaaS application security. The technology enables administrators to define access policies based on users’ roles and needs, ensuring that only authorised people access critical resources. The use of enhanced authentication methods, such as multi-factor authentication, adds an extra layer of security to prevent unauthorised access.
Security Orchestration
This automates the application of security policies, such as updating passwords and deactivating inactive accounts. It also manages security updates and patches for SaaS applications, ensuring that applications are always protected against known vulnerabilities. This automation ensures that security measures are applied consistently and effectively.
Risk and Compliance Management
The technology continuously assesses the risks associated with SaaS applications and generates detailed reports on their use and compliance with security standards. These reports help businesses demonstrate their commitment to security and comply with regulations. Continuous risk assessment enables risks to be identified and mitigated before they become major problems.
Security awareness
Technology’s security awareness programmes help employees to understand and adopt security best practice. By regularly participating in these programmes, employees become key players in the company’s security, helping to maintain a high level of security awareness.
Conclusion
By using a SaaS security solution to discover, inventory, monitor and secure SaaS applications, while actively involving employees in the security process, you need to assess your SaaS security needs and consider adopting the right solution to protect sensitive data, ensure compliance and prevent cyber-attacks. We can help you adopt this innovative approach and strengthen the security of your infrastructure and data.