The first step to impeccable Financial Security
When cyber security becomes a matter of survival, digital resilience is no longer an option, but a necessity. Faced with an increasing number of sophisticated cyber attacks and security flaws (APIs, CICD, Software Supply Chain, Bots, DDoS, Trojan Horses, etc.), digital resilience has become an absolute necessity. The European Union’s DORA (Digital Operational Resilience Act) regulations, which come into force in January 2023, provide a crucial framework for strengthening this resilience. But complying with these standards is only the first step in protecting against cyber threats. To ensure true security and seamless business continuity, businesses need to go beyond mere regulatory requirements.
General framework of DORA regulations
DORA’s objective
The main objective of DORA is to strengthen the digital operational resilience of the financial sector. This means that all financial entities must be able to withstand, respond to and recover quickly from disruptions related to Information and Communication Technologies (ICT). Coming into force on 16 January 2023, from 17 January 2025, this regulation will apply to all financial entities and critical ICT service providers.
Scope and Applicability
DORA is primarily concerned with:
- Banks
- Insurance companies
- Asset management companies
- Exchanges and trading platforms
- Payment and settlement institutions
These regulations also apply to critical ICT service providers:
- Cloud service providers
- Software as a Service (SaaS)
- Companies providing data storage services
- Providers of critical IT infrastructure
- Payment and transaction processing service providers
The implications are far-reaching, affecting both large financial institutions and smaller businesses that depend on ICT for their critical operations.
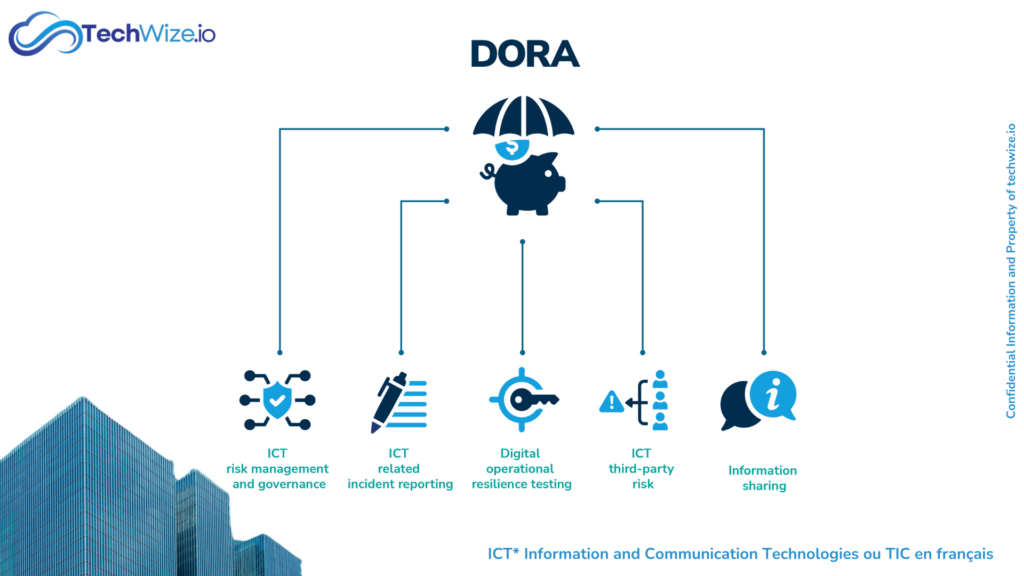
DORA Key Requirements
ICT Risk Management
ICT risk management is at the heart of DORA. Financial entities need to identify and assess potential ICT-related risks that could affect their operations or data security (data breaches, system failures, software incompatibility, third-party failures, compliance risks). This involves developing clear information security policies that define expectations, responsibilities and procedures for protecting digital assets.
Security Controls
DORA requires rigorous technical and organisational controls to be in place to prevent, detect and respond to security incidents. Companies must ensure that their systems are protected against cyber-attacks and other threats, and that they have processes in place to respond quickly and effectively in the event of an incident.
Technical controls
- Identify, document and manage all ICT risks that could affect their financial services.
- Implementing robust security measures to protect data integrity, authenticity and confidentiality.
- Carrying out regular tests to assess the effectiveness of security measures and their ability to withstand different types of cyber-attack.
Organisational controls
- Establishment of clear governance with defined roles and responsibilities for ICT risk management.
- Ongoing staff training on ICT risks and security procedures.
- Development of action plans to respond quickly and effectively to security incidents
These are onerous and time-consuming procedures, which is why companies are advised to adopt the right tools now!
Training and awareness
Staff training and awareness-raising are essential for effective data protection. DORA asks financial entities to set up training programmes for staff, to pass on best practice in ICT security.
Management Process and Governance
Incident Management
DORA entities must establish incident response plans to react quickly and effectively in the event of a security problem. These plans must include clear procedures for detecting, reporting and managing incidents, thereby minimising their impact on operations.
Business Continuity
DORA stresses the importance of business continuity and disaster recovery plans. These plans should ensure that critical operations can continue, even in the event of a major disruption, thereby ensuring the operational resilience of the business.
Audit and Review
Regular audits are essential to verify compliance with security policies and controls. Financial entities should also periodically review their processes to ensure they remain relevant in the face of evolving threats.
ICT governance
Appropriate ICT governance is crucial. DORA requires a strong commitment from senior management to support security initiatives and ensure that ICT risk management strategies are effectively implemented and monitored.
Monitoring of ICT Service Providers
Monitoring mechanism
DORA provides for the establishment of a mechanism for the direct supervision of critical ICT service providers at EU level. This means that businesses must ensure that their ICT service providers comply with the requirements of DORA, thereby strengthening the resilience of the financial sector as a whole.
Provider Compliance
Financial entities have a responsibility to ensure that their ICT service providers comply with the standards and requirements set out by DORA. This includes implementing controls to verify compliance and proactively managing the risks associated with external providers.
Associated Directive (EU) 2022/2556
In order to harmonise with the new provisions of DORA, Directive (EU) 2022/2556 amends several existing directives, (CRD IV, PSD2, BRRD, Solvency 2, IORP 2, MiFID 2, AIFM). This harmonisation aims to ensure regulatory consistency and facilitate the integration of new requirements.
Going beyond Compliance: Towards Sustainable Financial Security
The DORA regulation is the European Union’s response to the ICT threats facing the financial sector. Its aim is to raise security standards for businesses.
That’s why strict compliance with these directives is only the beginning of the journey towards enhanced digital security. Cyber attacks are agile, intelligent, defying boundaries and predictions. It is crucial to understand that regulatory compliance alone cannot guarantee robust security. Vulnerability is amplified by the increasing complexity of its infrastructures, whether on-premises or in the cloud.
It is imperative to use appropriate solutions and discuss them with cybersecurity experts to ensure highly effective protection. Organisations in the financial sector need to take immediate steps to strengthen their cyber security posture. To protect themselves, they can use agile solutions on niche themes such as APIs, CI/CD, WAF, IAM, DDoS, Anti-Bot, CDNs and Kubernetes.
Neglecting to strengthen security exposes your business to serious risks, with potentially damaging reputational consequences. By adopting a preventative approach and continuing to improve security, your business can not only comply with regulations, but also strengthen its resilience in the face of emerging threats. Only a continuous commitment to improving security can guarantee lasting protection over time.

