NEWS
Themes
Articles
-

ShadowIT: Risks, Causes, and Prevention
Understanding shadow IT Shadow IT refers to the unauthorized use of software such as SaaS and cloud services within a company, without the knowledge of the IT department. Shadow IT…
-
Protecting Data Transfers: A Cyber Security Priority
In today’s digital world, cybersecurity has become a major concern for businesses and individuals alike. Protecting data transfers is essential to ensuring the confidentiality and integrity of sensitive information. This…
-
The SaaS application wall: understanding the risks and protecting against them.
With the rise of SaaS (Software as a Service) applications in businesses, the number of entry keys is multiplying, posing a real security problem. This article aims to raise awareness…
-
A collaborative, behavioral approach: Redefining cybersecurity
With cyberthreats constantly evolving, the need for effective cybersecurity solutions to safeguard sensitive infrastructures and data has never been more pressing. The challenge is daunting: how can you effectively protect…
-
360° Digital Security: Managing your attack surface
In today’s digital world, every business, whatever its size or sector of activity, faces a multitude of security threats. One of the main concerns must be the company’s attackable surface,…
-

WAF and AI: An indestructible duo at your service
ANSSI reports that the number of reported intrusions will increase by 37% by 2021. Given this figure, web application security must become your priority. Web Application Firewalls (WAFs) protect web…
-

Virtual Machines (VMs) : Flexibility and Security
Whether for developers, businesses or home users, Virtual Machines (VMs) are the new standard of excellence in IT management. VMs make it possible to optimise the use of resources, improve…
-
Intrusion testing at the heart of an overall protection strategy
Current digital challenges With cyber risk on the rise, increasingly sophisticated cyber attacks are jeopardising data security and business continuity. It is therefore becoming normal practice to carry out a…
-

Honeypots: Your cybersecurity in rocket mode
The world of Honeypots Honeypots are the order of the day, a secret ally that lures cybercriminals into a trap, revealing their tactics and giving you the upper hand. In…
-

CIAM and IAM: From Internal Security to Customer Experience
IAM and CIAM at Your Company’s Service Data security and customer experience are at the heart of every company’s concerns. Identity and Access Management (IAM) and Customer Identity and Access…
-
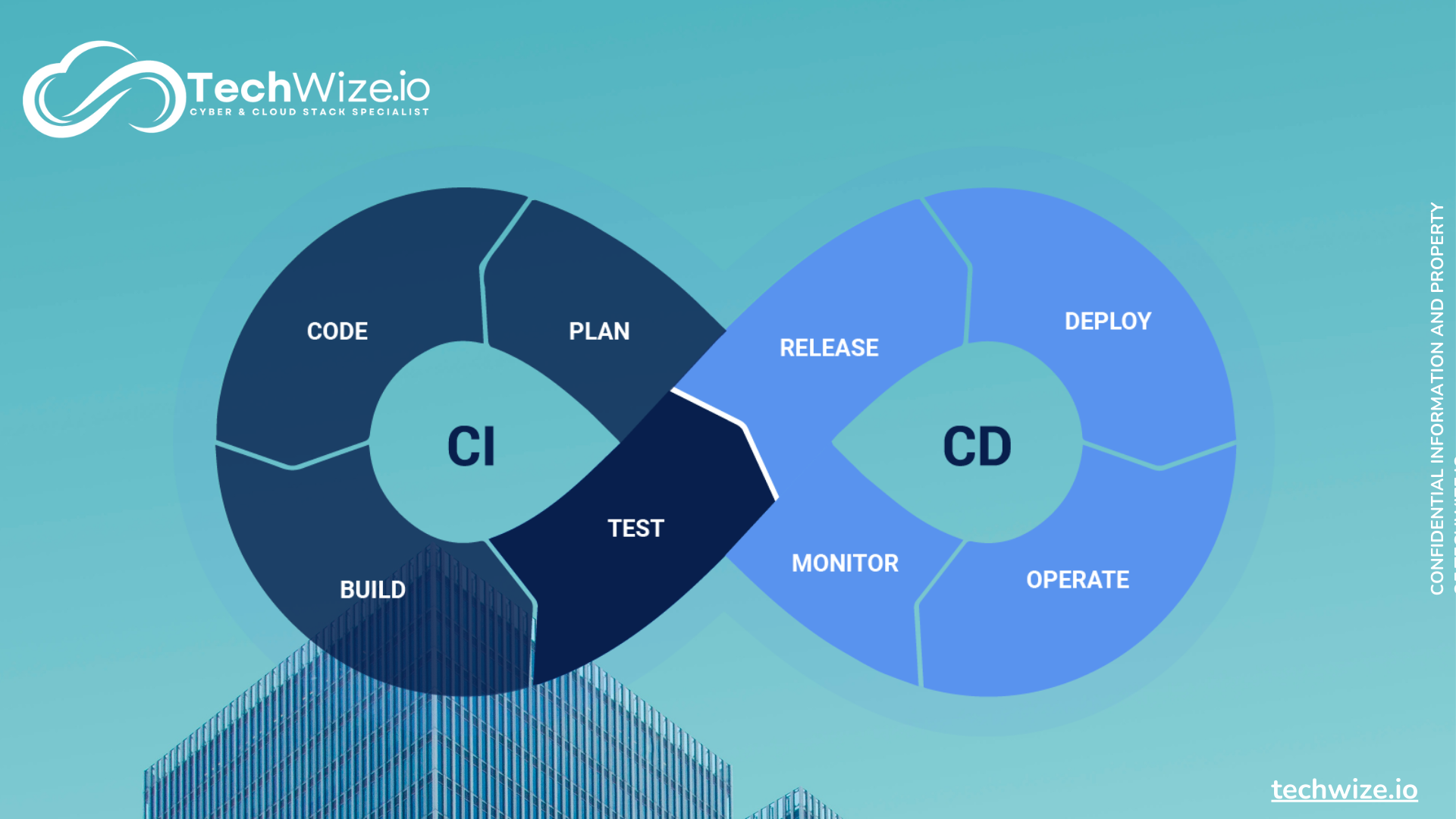
Software Supply Chain and CI/CD: revolutionise your software development
A new era in software development In the fast-paced, demanding world of software development, companies of all sizes are looking for ways to deliver quality software at unprecedented speed. That’s…
-

DORA: A response to Cyber Attacks in the financial sector.
The first step to impeccable Financial Security When cyber security becomes a matter of survival, digital resilience is no longer an option, but a necessity. Faced with an increasing number…
-

SOC2: The Security and Compliance Officer for Cloud and Technology Players
The Era of Digital Compliance The SAS70 standard has been a benchmark for the assessment of internal controls in organisations since its introduction in 1992. However, as data security and…
-

NIS2: Strengthening Cybersecurity in Europe for a Safer Digital Future
Guarantor of Digital Security in Europe If you’re a CISO, DPO or cybersecurity legal expert, you can’t escape NIS2, a major piece of European Union cybersecurity legislation. How does it…
-

The Content Delivery Network (CDN) Revolution: The Era of the Virtual Edge
Introduction In a world where consumer expectations are constantly evolving, speed has become essential. Online content delivery is now a key pillar of this revolution. Content Delivery Networks are key…
